Privacy-Preserving Authentication Methods
Implementing zero-knowledge proofs and other privacy-focused authentication systems.
Introduction
Authentication today often exposes personal identifiers (usernames, emails) to service providers or identity platforms, creating privacy risks. For example, social logins (OAuth) link your real identity to apps, and password databases have been breached repeatedly. Privacy-preserving authentication aims to verify user credentials without revealing any unnecessary information. Zero-knowledge proofs (ZKPs) enable exactly this: a user proves they possess valid credentials (e.g. a password or OAuth token) without disclosing them.
Modern research finds ZKP-based schemes offer "a superior framework for privacy-preserving authentication", mitigating vulnerabilities of traditional logins. This is critical for web2 and web3 alike as identity leaks can lead to targeted attacks or censorship. By proving authorization in zero knowledge, new authentication methods can keep users' identities confidential and unlinkable across platforms.
Concepts Recap
A zero-knowledge proof (ZKP) is a protocol where a prover convinces a verifier of a statement's truth without revealing why it's true. Modern ZKP systems are usually non-interactive (via Fiat–Shamir transform) and fall into a few categories:
-
zk-SNARKs (Succinct Non-interactive ARguments of Knowledge): These produce very short proofs (hundreds of bytes) that verify quickly, even for complex statements. However, SNARKs typically require a one-time trusted setup ceremony to generate a common reference string (CRS). This setup (e.g. Groth16 or PLONK ceremonies) must be done securely; if compromised, the system's soundness is at risk. In practice, SNARKs have been used in protocols like Zcash and Sui's zkLogin.
-
zk-STARKs (Scalable Transparent ARguments of Knowledge): Introduced around 2018, STARKs avoid any trusted setup by using only public randomness and polynomial commitments. They are scalable and quantum-resistant, but STARK proofs are much larger (tens of kilobytes) and slower to generate than SNARKs. They trade proof size and generation time for transparency (no trusted setup) and post-quantum security.
-
Bulletproofs: A type of ZKP especially efficient for range proofs (proving a secret value is in a range) without trusted setup. Bulletproofs are short (on the order of 1–1.5 KB) and do not require a ceremony. They are used in confidential transaction systems (e.g. Monero). In general, Bulletproofs generate proofs by aggregating multiple range proofs and are smaller than STARK proofs while still avoiding trusted setup.
SNARKs and Bulletproofs both yield very succinct proofs, but SNARKs need a trusted CRS setup while Bulletproofs and STARKs do not. The choice of proof system is a tradeoff between proof size, trust assumptions, and computational cost.
Beyond these, new proof systems like PLONK, Halo2, and Nova aim to balance efficiency with transparent setup. Interactive ZKPs (where the prover and verifier exchange multiple messages) are less common in practice, as authentication generally uses non-interactive proofs verified in one step. The goal across all these protocols is to prove statements (e.g. "I know the password for account X" or "I am a member of group Y") without revealing the password or identity itself.
Implementation Landscape
A variety of libraries and frameworks support building ZK-based authentication:
Circom + snarkJS (JavaScript)
A popular stack for web developers. Circom is a DSL for writing arithmetic circuits; snarkJS provides the proving system. For example, one can compile a Circom circuit to WASM and generate a proof in Node.js. In code, Groth16 proof generation looks like:
const { proof, publicSignals } = await snarkjs.groth16.fullProve(
{ a: 11, b: 3 },
"circuit.wasm",
"circuit_final.zkey"
);
console.log(publicSignals, proof);
This runs a trusted setup and produces a proof that a * b = 33 without revealing a and b. The snarkJS CLI and Circom library are open-source and widely used (see the Circom docs and snarkjs repo).
ZoKrates (Rust/C++)
A high-level toolbox for zk-SNARKs (especially on Ethereum). It provides a custom DSL, a compiler, and CLI tools to perform setup, witness computation, proof generation, and on-chain verification. ZoKrates is designed for developers integrating ZKPs into smart contracts. The official repository and tutorials walk through writing a program, running a setup ceremony, and generating proofs.
Gnark (Go)
A Go library by ConsenSys for building ZK circuits. It supports Groth16 and PLONK and offers an intuitive API. For example, developers can define a Go struct for a statement and let gnark synthesize the constraint system. Gnark is optimized for performance and was specifically created to make SNARK proofs easy in Go.
Noir (Rust)
A newer DSL (by Aztec) for writing ZK circuits in a Rust-like syntax. Noir compiles to ACIR and supports various proving backends (e.g. Groth16). It aims to simplify circuit development and integrates with modern toolchains.
Arkworks / bellman (Rust/C++)
Low-level libraries and frameworks for SNARK and STARK protocols. Arkworks is a modular Rust library covering many elliptic curves and proof systems. Developers can build custom ZK schemes (Groth16, Marlin, etc.) using Arkworks' traits. Bellman is another SNARK library (used in Zcash). These libraries are more cryptographic and are used in production systems (e.g. blockchain clients).
Semaphore and other ZK protocol libraries
Higher-level libraries focused on specific use cases. For instance, Semaphore (by the PSE team) provides JavaScript tools for anonymous signaling and group membership proofs. It includes identity and group abstractions, proof generation, and smart contracts for on-chain verification. Anoiden's SSO system (see below) is built on Semaphore's JS libraries.
Many modern ZKP frameworks include high-level languages and tooling to hide low-level cryptography. For example, Circom/ZoKrates handle setup and proof steps for you, and Noir offers a Rust-like syntax. This helps bridge ZKP complexity for developers.
Code Example: Generating a ZK Proof
Below is a snippet (using snarkJS) that shows how a developer might generate a proof in code. In practice, you would first compile your circuit (e.g. a Circom circuit) to WASM and run a setup ceremony to get a .zkey file. The fullProve call below takes input values, the compiled circuit, and the proving key, then returns the proof and public outputs:
const { proof, publicSignals } = await snarkjs.groth16.fullProve(
{ secret: 123 }, // private inputs (the prover's secret)
"build/circuit.wasm", // compiled circuit
"circuit_final.zkey" // proving key after setup
);
console.log(publicSignals, proof);
// The verifier can then check the proof against publicSignals.
This example is adapted from the Circom/snarkjs tutorial.
Code Example: Semaphore Proof
For group membership or identity proofs (as in Anoiden), a library like Semaphore provides convenience functions. For example, after setting up an identity and group, one can generate a proof with:
// Using Semaphore.js (pse.dev library):
await generateProof(identity, group, nonce, "signIn");
Here, identity is the user's ZK identity object, group is a Merkle-tree group of identities, and nonce is a challenge from the verifier. This single line uses Semaphore's JS library to compute a ZK proof of membership.
Architecture Patterns
In ZK-based authentication, the user typically obtains a credential (or secret) from an identity provider, then uses it to generate a ZK proof for the service provider, without revealing the credential itself. Two real-world examples illustrate different approaches:
Anoiden (Zero-Knowledge SSO with Semaphore)
Anoiden is a prototype ZK single sign-on system built on Ethereum's research forum. The user first "connects" their identity by registering with an Identity Provider (IdP) and linking a ZK identity. During Connect, a browser extension interacts with the IdP: it requests the user's identifiers, generates a Semaphore identity, and uses it to sign a nonce from the IdP. The extension calls await generateProof(identity, group, nonce, "signIn") to create this proof. The IdP verifies this proof, adds the user's identifier into a Merkle tree, and returns a signature.
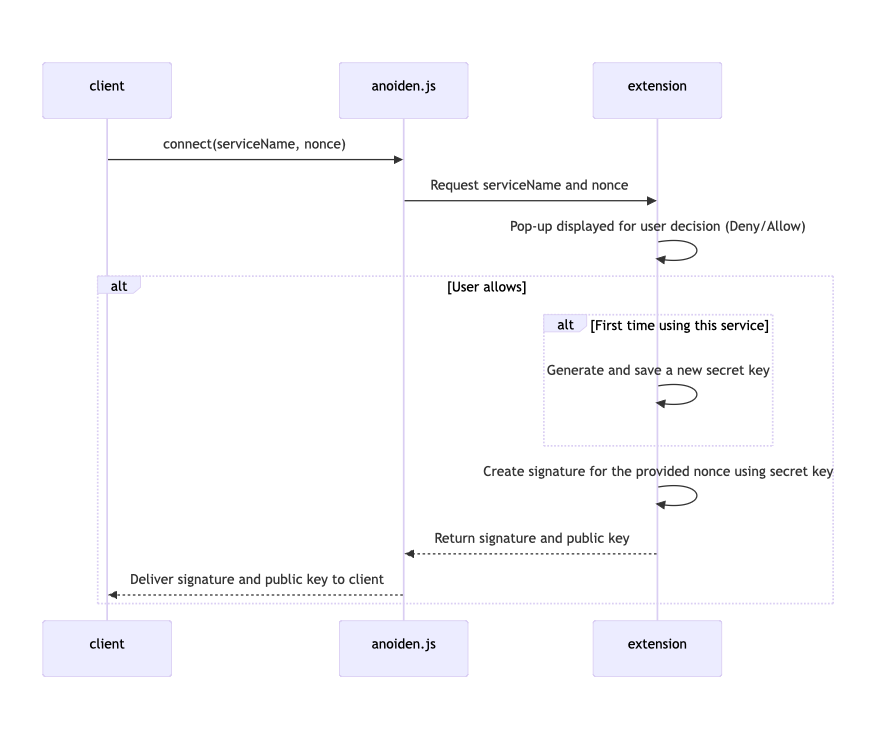 – the user's browser extension requests identifiers and generates a ZK proof for the IdP.
– the user's browser extension requests identifiers and generates a ZK proof for the IdP.
The diagrams below show the flow. In the first part [above], the client extension (via anoiden.js) requests the user's ID list from the IdP, then generates a Semaphore proof using the received identifiers and the SP-provided nonce. In the second part, the client sends this proof, and the server verifies it. If valid, the IdP signs the authentication challenge and completes the registration.
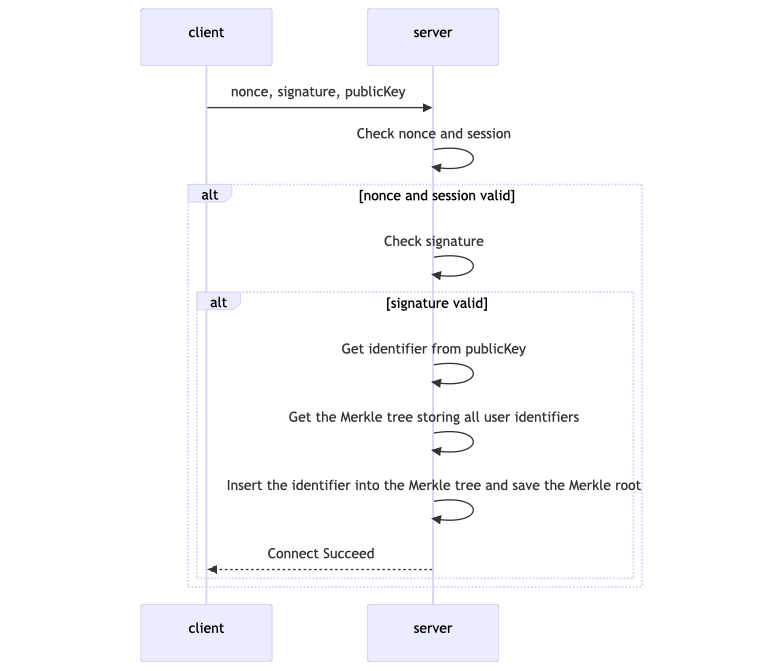 – the IdP verifies the proof, updates the Merkle tree of identities, and returns a signed credential.
– the IdP verifies the proof, updates the Merkle tree of identities, and returns a signed credential.
For the Auth phase, when the user later wants to sign in to a Service Provider (SP), the extension again fetches an authentication nonce from the SP. It then uses Semaphore to prove membership in the IdP's registered group without revealing which member it is. The IdP checks the proof against the nonce, and if valid, issues a signature for the SP to accept. The flow is illustrated below.
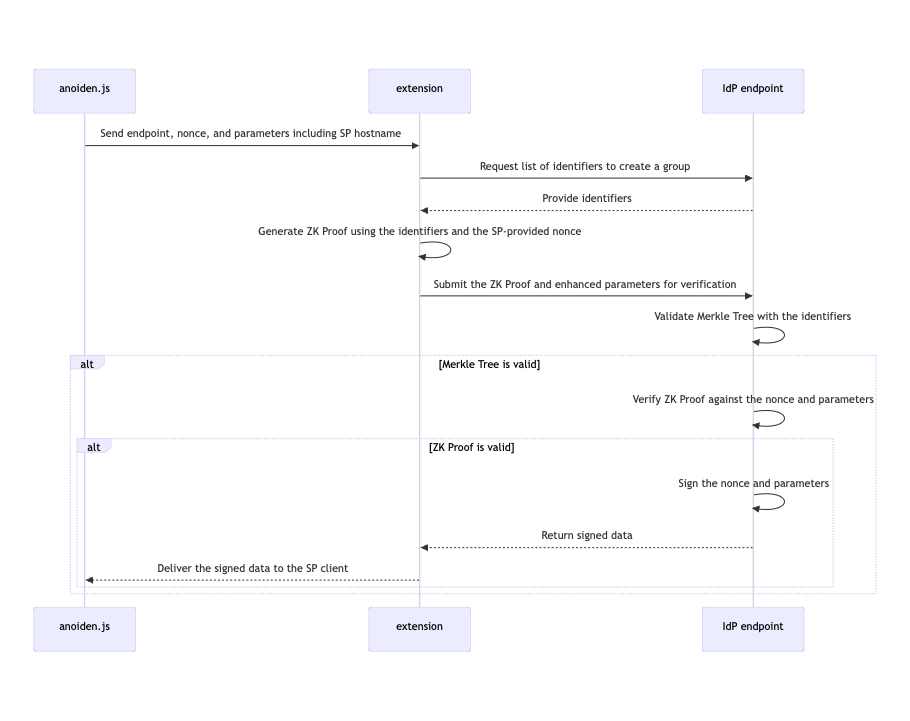 – the client generates a ZK proof and the IdP verifies it before signing an authentication token for the SP.
– the client generates a ZK proof and the IdP verifies it before signing an authentication token for the SP.
In this Anoiden flow, notice that the IdP never learns which group member is authenticating. Even colluding IdP and SP cannot link the login to the specific user. After proof verification, the SP simply sees a valid signature on the nonce. The security relies on the zero-knowledge property of the Semaphore proof and on the integrity of the signed credential.
Sui's zkLogin (OAuth + ZKP)
Sui (a novel blockchain) implements a native ZK login called zkLogin. The user logs in with an OAuth/OpenID provider (e.g. Google) to obtain a JWT that includes a "nonce" field. The wallet generates a one-time key pair whose public key is embedded in that nonce. Next, the wallet submits the JWT to a salt server to get a unique user_salt. This salt (derived from a secret master seed) prevents linking the JWT to the on-chain address.
The JWT and salt are sent to a ZK proving service, which checks the JWT's signature and nonce structure, and proves that the user knows the OAuth secret and the salt aligns with their address. Finally, the wallet signs a Sui transaction with the ephemeral private key and submits it along with the ZK proof.
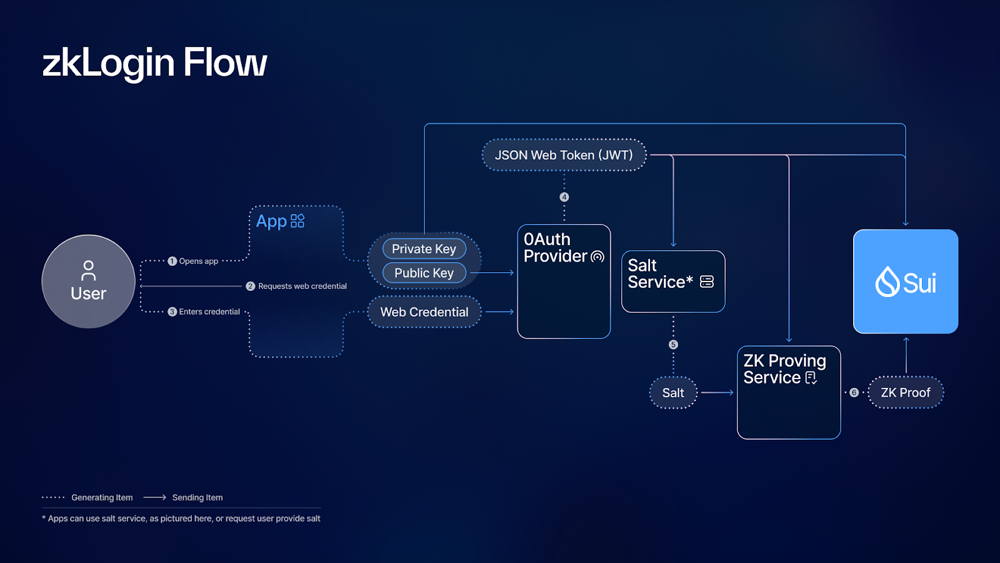 – the user obtains a JWT from an OAuth provider, fetches a salt from a salt service, then generates a ZK proof of authorization for a Sui transaction.
– the user obtains a JWT from an OAuth provider, fetches a salt from a salt service, then generates a ZK proof of authorization for a Sui transaction.
In Sui's design, the salt server (often run in a trusted enclave) supplies a fresh random salt tied to the user's OAuth token. This salt is the extra secret that ensures a compromised OAuth account cannot authorize transactions on its own. Sui's authorities then verify the Groth16 ZK proof on-chain, which confirms the JWT is valid and the address derivation is correct, without revealing the user's OAuth identifier. The result: a user can transact on Sui "as themselves" (same address each time) without the OAuth provider ever learning which address it is, preserving privacy.
These examples highlight common ZK-auth architecture: an ID provider issues some credential or challenge, the user proves possession via ZKP (using libraries like Semaphore or snarkJS), and a verifier checks the proof (possibly on-chain) without learning sensitive details. The diagrams above (Anoiden and zkLogin) show how the flows work in practice.
Comparison Table
System | Privacy (info revealed) | Trust Model / Setup | User UX | Example |
|---|---|---|---|---|
| Password Login | Username plus password (usually hashed on server). Service sees user identity directly. | User trusts server to store password hash securely. | Users must remember password; susceptible to phishing or reuse attacks. | Traditional websites with login forms. |
| OAuth2 / Social Login | User email/ID is shared from provider to app. The app learns your identity or social profile. | User trusts third-party provider (Google, Facebook) and app with identity info. | Single-click login via popup/redirect. Familiar flow but links across services. | "Sign in with Google" on websites/apps. |
| WebAuthn (FIDO2) | No password; authenticator holds private key. Relying Party gets a public key ID (user account ID). | Security via public-key; relies on hardware (token or TPM) and RP's attestation. | Passwordless: user taps a security key or uses platform biometrics. Phishing-resistant. | YubiKey or built-in device authenticators on supporting sites. |
| 2FA (TOTP/SMS) | Requires initial user identifier (email/phone); then a one-time code. The code itself reveals nothing beyond possession. | User trusts token generator (auth app or SMS provider) and service's auth system. | After entering password, user inputs a time-based code or SMS code. Extra step but widely used. | Google Authenticator codes; SMS code login. |
| ZKP-based Login | Minimal: proves valid credential without revealing the credential itself. In some schemes, no direct link between on-chain address and identity. | Relies on cryptographic assumptions and system setup (e.g. a trusted ZK ceremony or secure salt server). | Similar to social login UX: user authenticates (e.g. via OAuth), then the wallet generates a ZK proof under the hood. The end-user sees a familiar OAuth login followed by a transparent approval. | Sui's zkLogin (OAuth + ZK proof); anonymous SSO (Anoiden) using Semaphore. |
Challenges & Tradeoffs
While ZK-based authentication offers strong privacy, it introduces new complexity:
Performance & Scalability
ZK proofs (especially SNARK/STARK proofs) require significant computation. Proof generation can take anywhere from milliseconds to seconds on modern hardware, depending on the circuit complexity. Large proofs (STARKs) take more bandwidth. Verifying proofs is usually faster but still costlier than checking a password. These costs can hinder large-scale adoption, though ongoing research is reducing proof sizes and speeds.
Development Complexity
Designing secure ZK circuits requires cryptographic expertise. Developers must reason about constraint systems and handle key management (e.g. keeping proving keys secret). This specialized knowledge and the relative scarcity of mature tooling can slow adoption. Higher-level frameworks (Circom, Noir) help, but learning curves remain.
Trust Assumptions
Many ZK systems still depend on setup/trust: SNARKs need a secure ceremony; Sui's zkLogin needs a trusted salt server environment. Compromise of these (e.g. dishonest contributor to a setup, or a leaked salt seed) can break privacy or security. STARKs avoid the trusted setup but introduce larger proofs. Each approach has tradeoffs: no setup vs. trusted randomness, which affects developer trust models.
UX and Adoption
For end-users, ZK-auth typically relies on existing auth flows (OAuth, wallets) plus a proof step. While modern UIs can hide the complexity, longer delays for proof generation or additional steps (e.g. fetching a salt) may hurt user experience. Wallet interoperability and key backup are also considerations. Developers and organizations must balance privacy gains against the costs of integrating new infrastructure.
Trust & Security
ZK proofs only ensure cryptographic validity of credentials. They don't prevent user mistakes (e.g. logging into a phishing fake that simply verifies a proof). Systems must still ensure domain binding and prevent replay attacks (nonces, expiration). Also, as with any crypto, underlying assumptions (e.g. hardness of discrete log) must hold.
Despite these challenges, recent audits and protocols have demonstrated that well-engineered ZK-auth can be practical. For instance, Sui's zkLogin implementation has been independently audited and uses a rigorous ceremony to generate its proving keys, ensuring a high confidence in its setup. As the technology matures, many of these tradeoffs are being addressed by more efficient proof systems and better developer tools.
Future Outlook
The ZK authentication ecosystem is rapidly evolving. Key trends include:
Ecosystem Maturation
More blockchains and services are building native ZK-auth. For example, beyond Sui, some Ethereum projects experiment with ZK credentials. Developer libraries (Circom, Noir, Halo2) are improving toolchains, lowering barriers to entry. Established protocols like WebAuthn may even incorporate ZKP concepts in the future.
Standardization Efforts
We expect standard frameworks for ZK-credentials to emerge (similar to OAuth/OpenID). Workgroups like ZKProof (IC3) and industry alliances may define interoperable proof formats. Integration with decentralized identity (DID) standards is a possibility. This will help developers adopt ZK-auth in a consistent way.
UX and Tooling
Improved UX is on the horizon. For instance, using trusted hardware enclaves (TPM, Secure Enclave) or secure elements can speed up proof generation and protect keys without user friction. Cloud-based ZK proof services (e.g. hosted proving servers) may abstract complexity away from clients. Libraries will provide higher abstractions so that product developers need not write circuits by hand.
Cryptographic Innovations
New proof systems are emerging. Recursive SNARKs and proof aggregation (as in Halo2's recursive proofs) can shrink multi-step verification into one succinct proof. Novel setups (e.g. transparent universal ceremonies) reduce trust assumptions. STARKs continue to get faster, and hybrid protocols (mixing SNARK and STARK) aim to get the best of both. These advances will lower computation and bandwidth costs. As one review notes, optimizing efficiency and usability is crucial to ZKP adoption.
Broader Adoption
As privacy regulations tighten (e.g. GDPR) and users demand data minimization, privacy-preserving auth may become a selling point. Financial and healthcare industries, in particular, are interested in attribute-based ZK-auth (proving you are over 18 or a valid member) without revealing identity. Projects like anonymous credentials (Idemix, Microsoft's Coco framework) and decentralized KYC are under active development.
In summary, the field is moving from theory to practice. Promising research and corporate R&D are converging: ZK proofs are likely to become a standard tool for authentication and identity in the coming years.
Conclusion and Further Reading
Zero-knowledge proofs offer a powerful new way to authenticate users privately. By revealing only the validity of credentials, ZK-based systems can dramatically improve user privacy compared to passwords or OAuth2 (which fully expose identity). Real implementations like Sui's zkLogin and Semaphore-based SSO (Anoiden) demonstrate that these ideas can work end-to-end. However, they come with tradeoffs in complexity, performance, and trust assumptions. As the cryptography and blockchain communities refine protocols and tooling, we expect ZK authentication to become more efficient and easier to use. For readers interested in exploring further, consider the following authoritative resources:
- Bhattacharya et al., "Enhancing Digital Privacy: The Application of ZKPs in Authentication Systems" (2024) – A survey of ZKP in authentication, detailing theoretical foundations and comparisons.
- Sui Foundation's zkLogin documentation – Official docs explaining Sui's privacy-preserving login flow and its security goals.
- Semaphore protocol repository and docs – Includes the libraries and contracts for anonymous group proofs, used in ZK-SSO examples.
- Circom/snarkJS official docs – Guides on writing ZK circuits and generating proofs in JavaScript (see https://docs.circom.io/ and https://github.com/iden3/snarkjs).
- ZoKrates documentation – Tutorials for building zk-SNARK programs on Ethereum (https://zokrates.github.io/).
These resources, along with the referenced literature, provide detailed explanations and examples to deepen understanding of ZKP-based authentication. As a cutting-edge topic, it pays to keep an eye on conferences (e.g. ZKProof Workshop, Crypto) and community forums for the latest developments.
References
- Enhancing Digital Privacy: The Application of Zero-Knowledge Proofs in Authentication Systems
- zkLogin | Sui Documentation
- Crypto Bulletproofs – An Introduction
- JavaScript tutorial for Zero-Knowledge Proofs Using SnarkJS and Circom
- Ultimate Guide to Zero-Knowledge Proof Libraries and Tools in 2024
- Exploring SNARK Interoperability in Rust and Go
- GitHub - semaphore-protocol/semaphore: A zero-knowledge protocol for anonymous interactions
- Anoiden: Zero Knowledge SSO with Semaphore
- Sui zkLogin Salt Server Architecture